Azure Security and Compliance Blueprint: PaaS Web Application for FedRAMP #
Overview #
The Federal Risk and Authorization Management Program (FedRAMP) is a United States government-wide program that provides a standardized approach to security assessment, authorization, and continuous monitoring for cloud products and services. This Azure Security and Compliance Blueprint provides guidance for how to deliver a Microsoft Azure platform as a service (PaaS) architecture that helps implement a subset of FedRAMP High controls. This solution provides guidance on the deployment and configuration of Azure resources for a common reference architecture, demonstrating ways in which customers can meet specific security and compliance requirements and serves as a foundation for customers to build and configure their own solutions on Azure.
This reference architecture, associated control implementation guides, and threat models are intended to serve as a foundation for customers to adjust to their specific requirements and should not be used as-is in a production environment. Deploying an application into this environment without modification is insufficient to completely meet the requirements of the FedRAMP High baseline. Please note the following:
- The architecture provides a baseline to help customers deploy workloads to Azure in a FedRAMP-compliant manner.
- Customers are responsible for conducting appropriate security and compliance assessments of any solution built using this architecture, as requirements may vary based on the specifics of each customer’s implementation.
A complete list/map of all FedRAMP requirements can be found here along with how and why Sphera meets or exceeds each of those requirements.
Architecture diagram and components #
This solution provides a reference architecture for a PaaS web application with an Azure SQL Database backend. The web application is hosted in an isolated Azure App Service Environment, which is a private, dedicated environment in an Azure datacenter. The environment load balances traffic for the web application across VMs managed by Azure. This architecture also includes network security groups, an Application Gateway, Azure DNS, and Load Balancer. Furthermore, Azure Monitor provides real-time analytics of system health. Azure recommends configuring a VPN or ExpressRoute connection for management and data import into the reference architecture subnet.
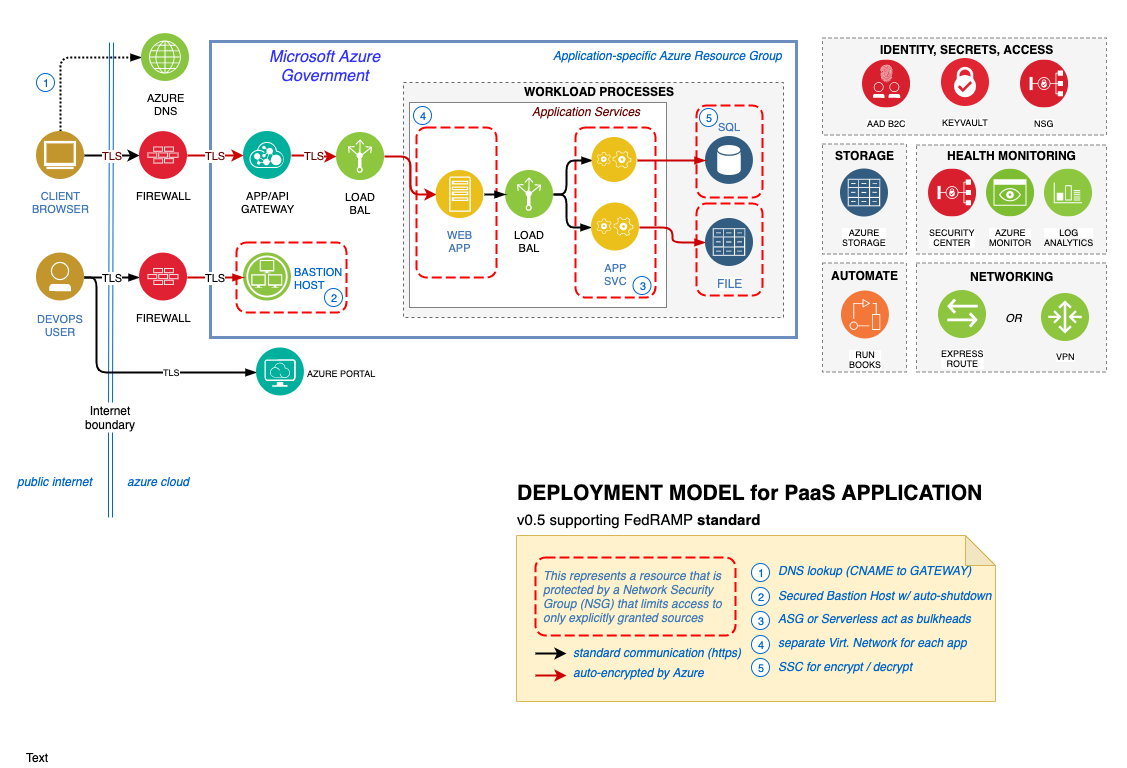
Deployment architecture #
The following section details the deployment and implementation elements.
Azure Resource Manager: Azure Resource Manager enables customers to work with the resources in the solution as a group. Customers can deploy, update, or delete all the resources for the solution in a single, coordinated operation. Customers use a template for deployment and that template can work for different environments such as testing, staging, and production. Resource Manager provides security, auditing, and tagging features to help customers manage their resources after deployment.
App Service Environment v2: The Azure App Service Environment (ASE) is an App Service feature that provides a fully isolated and dedicated environment for securely running App Service applications at a high scale.
ASEs are isolated to only run a single customer’s applications and are always deployed into a virtual network. Customers have fine-grained control over both inbound and outbound application network traffic, and applications can establish high-speed secure connections over virtual networks to on-premises corporate resources.
Use of ASEs for this architecture are allowed for the following controls/configurations:
- Host inside a secured Azure Virtual Network and network security rules ASE configured with self-signed ILB certificate for HTTPS communication
- Internal Load Balancing mode
- Disable TLS 1.0
- Change TLS Cipher
- Control inbound traffic N/W ports
- Web Application Firewall – Restrict Data
- Allow Azure SQL Database traffic
The Guidance and recommendations section contains additional information about ASEs.
Azure Web App: Azure App Service enables customers to build and host web applications in the programming language of their choice without managing infrastructure. It offers auto-scaling and high availability, supports both Windows and Linux, and enables automated deployments from GitHub, Azure DevOps, or any Git repo.
Virtual Network #
The architecture defines a private virtual network with an address space of 10.200.0.0/16.
Network security groups: Network security groups (NSGs) contain access control lists that allow or deny traffic within a virtual network. NSGs can be used to secure traffic at a subnet or individual VM level. The following NSGs exist:
- 1 NSG for Application Gateway
- 1 NSG for App Service Environment
- 1 NSG for Azure SQL Database
Each of the NSGs have specific ports and protocols open so that the solution can work securely and correctly. In addition, the following configurations are enabled for each NSG:
- Diagnostic logs and events are enabled and stored in a storage account
- Azure Monitor logs is connected to the NSG’s diagnostics
Subnets: Each subnet is associated with its corresponding NSG.
Azure DNS: The Domain Name System, or DNS, is responsible for translating (or resolving) a website or service name to its IP address. Azure DNS is a hosting service for DNS domains that provides name resolution using Azure infrastructure. By hosting domains in Azure, users can manage DNS records using the same credentials, APIs, tools, and billing as other Azure services. Azure DNS also supports private DNS domains.
Azure Load Balancer: Azure Load Balancer allows customers to scale their applications and create high availability for services. Load Balancer supports inbound as well as outbound scenarios, and provides low latency, high throughput, and scales up to millions of flows for all TCP and UDP applications.
Data in transit #
Azure encrypts all communications to and from Azure datacenters by default. All transactions to Azure Storage through the Azure portal occur via HTTPS.
Data at rest #
The architecture protects data at rest through encryption, database auditing, and other measures.
Azure Storage: To meet encrypted data at rest requirements, all Azure Storage uses Storage Service Encryption.
Azure Disk Encryption: Azure Disk Encryption leverages the BitLocker feature of Windows to provide volume encryption for data disks. The solution integrates with Azure Key Vault to help control and manage the disk-encryption keys.
Azure SQL Database: The Azure SQL Database instance uses the following database security measures:
- AD authentication and authorization enables identity management of database users and other Microsoft services in one central location.
- SQL database auditing tracks database events and writes them to an audit log in an Azure storage account.
- Azure SQL Database is configured to use Transparent Data Encryption (TDE), which performs real-time encryption and decryption of the database, associated backups, and transaction log files to protect information at rest.
- Firewall rules prevent all access to database servers until proper permissions are granted. The firewall grants access to databases based on the originating IP address of each request.
- SQL Threat Detection enables the detection and response to potential threats as they occur by providing security alerts for suspicious database activities, potential vulnerabilities, SQL injection attacks, and anomalous database access patterns.
- Always Encrypted Columns ensure that sensitive data never appears as plaintext inside the database system. After enabling data encryption, only client applications or application servers with access to the keys can access plaintext data.
- Row-Level Security enables users to define policies to restrict access to data to discontinue processing.
- SQL Database dynamic data masking can be done after the reference architecture deploys. We will need to adjust dynamic data masking settings to adhere to the database schema.
Identity management #
The following technologies provide identity management capabilities in the Azure environment:
- Azure Active Directory an Azure Active Directory B2C is Microsoft’s multi-tenant cloud-based directory and identity management service. All users for this solution are created in AAD or AAD B2C, including users accessing the Azure SQL Database.
- Authentication to the application is performed using AAD. For more information, see Integrating applications with Azure Active Directory. Additionally, the database column encryption uses Azure Active Directory to authenticate the application to Azure SQL Database. For more information, see how to protect sensitive data in Azure SQL Database.
- Azure role-based access control enables precisely focused access management for Azure. Subscription access is limited to the subscription administrator, and access to resources can be limited based on user role.
- Azure Active Directory Privileged Identity Management enables customers to minimize the number of users who have access to certain information. Administrators can use AAD Privileged Identity Management to discover, restrict, and monitor privileged identities and their access to resources. This functionality can also be used to enforce on-demand, just-in-time administrative access when needed.
- Azure Active Directory Identity Protection detects potential vulnerabilities affecting an organization’s identities, configures automated responses to detected suspicious actions related to an organization’s identities, and investigates suspicious incidents to take appropriate action to resolve them.
Security #
Secrets Management: The solution uses Azure Key Vault for the management of keys and secrets. Azure Key Vault helps safeguard cryptographic keys and secrets used by cloud applications and services. The following Azure Key Vault capabilities help customers protect data and access to such data:
- Advanced access policies are configured on a need basis. Key Vault access policies are defined with minimum required permissions to keys and secrets.
- All keys and secrets in Key Vault have expiration dates.
- All keys in Key Vault are protected by specialized hardware security modules (HSMs). The key type is an HSM Protected 2048-bit RSA Key. *All users and identities are granted minimum required permissions using role-based access control.
- Diagnostics logs for Key Vault are enabled with a retention period of at least 365 days.
- Permitted cryptographic operations for keys are restricted to the ones required.
Application Gateway: The architecture reduces the risk of security vulnerabilities using an Application Gateway with Web Application Firewall, and the OWASP ruleset enabled. Additional capabilities include:
- End-to-End-SSL
- Enable SSL Offload
- Disable TLS v1.0 and v1.1
- Web Application Firewall
- Prevention mode with OWASP 3.0 ruleset
- Enable diagnostics logging
- Custom health probes
- Azure Security Center and Azure Advisor provide additional protection and notifications. Azure Security Center also provides a reputation system.
Logging and auditing #
Azure Monitor provides extensive logging of system and user activity, as well as system health. It collects and analyzes data generated by resources in Azure and on-premises environments.
- Activity logs: Activity logs provide insight into operations performed on resources in a subscription. Activity logs can help determine an operation’s initiator, time of occurrence, and status.
- Diagnostic logs: Diagnostic logs include all logs emitted by every resource. These logs include Windows event system logs, Azure Storage logs, Key Vault audit logs, and Application Gateway access and firewall logs.
- Log archiving: All diagnostic logs write to a centralized and encrypted Azure storage account for archival. The retention is user-configurable, up to 730 days, to meet organization-specific retention requirements. These logs connect to Azure Monitor logs for processing, storing, and dashboard reporting.
Additionally, the following monitoring solutions are included as a part of this architecture:
- Active directory Assessment: The Active Directory Health Check solution assesses the risk and health of server environments on a regular interval and provides a prioritized list of recommendations specific to the deployed server infrastructure.
- Antimalware Assessment: The Antimalware solution reports on malware, threats, and protection status.
- Azure Automation: The Azure Automation solution stores, runs, and manages runbooks. In this solution, runbooks help collect logs from Application Insights and Azure SQL Database.
- Security and Audit: The Security and Audit dashboard provides a high-level insight into the security state of resources by providing metrics on security domains, notable issues, detections, threat intelligence, and common security queries.
- SQL Assessment: The SQL Health Check solution assesses the risk and health of server environments on a regular interval and provides customers with a prioritized list of recommendations specific to the deployed server infrastructure.
- Update Management: The Update Management solution allows customer management of operating system security updates, including a status of available updates and the process of installing required updates.
- Agent Health: The Agent Health solution reports how many agents are deployed and their geographic distribution, as well as how many agents which are unresponsive and the number of agents which are submitting operational data.
- Azure Activity Logs: The Activity Log Analytics solution assists with analysis of the Azure activity logs across all Azure subscriptions for a customer.
- Change Tracking: The Change Tracking solution allows customers to easily identify changes in the environment.
Azure Monitor: Azure Monitor helps users track performance, maintain security, and identify trends by enabling organizations to audit, create alerts, and archive data, including tracking API calls in customers’ Azure resources.
Threat model #
This model can help customers understand the points of potential risk in the system infrastructure when making modifications.
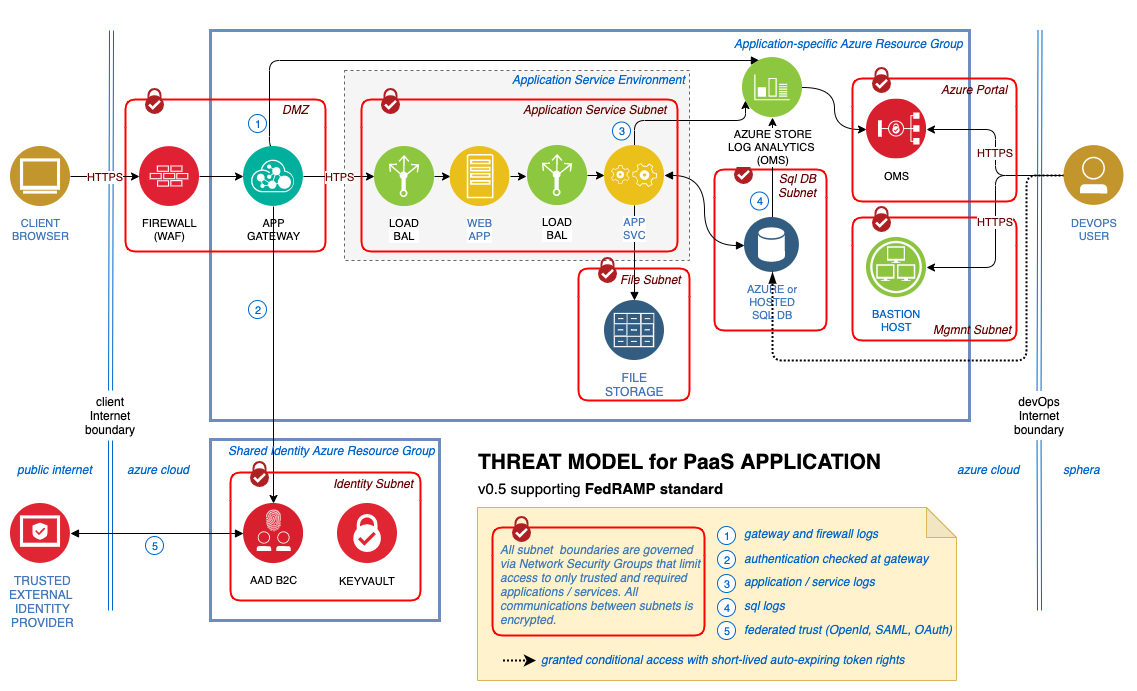
Compliance documentation #
The Sphera Security and Compliance Blueprint - FedRAMP PaaS WebApp High Control Implementation Matrix lists all security controls required by the FedRAMP High baseline. The matrix provides information on which controls are covered by the PaaS web application architecture, including detailed descriptions of how the implementation meets the requirements of each covered control.
Guidance and recommendations #
VPN and ExpressRoute #
A secure VPN tunnel or ExpressRoute needs to be configured to securely establish a connection to the resources deployed as a part of this PaaS web application reference architecture. By appropriately setting up a VPN or ExpressRoute, customers can add a layer of protection for data in transit.
By implementing a secure VPN tunnel with Azure, a VPN connection between an on-premises network and an Azure Virtual Network can be created. This connection takes place over the Internet and allows customers to securely “tunnel” information inside an encrypted link between the customer’s network and Azure. Site-to-Site VPN is a secure, mature technology that has been deployed by enterprises of all sizes for decades. The IPsec tunnel mode is used in this option as an encryption mechanism.
Because traffic within the VPN tunnel does traverse the Internet with a site-to-site VPN, Microsoft offers another, even more secure connection option. Azure ExpressRoute is a dedicated WAN link between Azure and an on-premises location or an Exchange hosting provider. As ExpressRoute connections do not go over the Internet, these connections offer more reliability, faster speeds, lower latencies, and higher security than typical connections over the Internet. Furthermore, because this is a direct connection of customer’s telecommunication provider, the data does not travel over the Internet and therefore is not exposed to it.
Best practices for implementing a secure hybrid network that extends an on-premises network to Azure are available.
